Possible uses of agents and gateways
Simple network
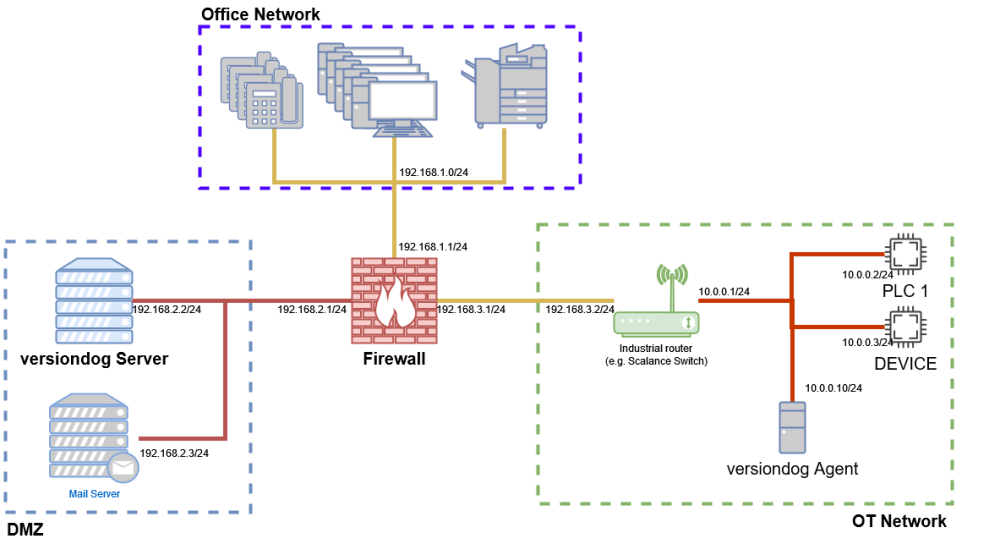
If our network is defined like below then the versiondog Server cannot access any PLC directly. Not only because the server is inside an isolated network (DMZ) but also because both PLC are inside their own OT-Network (which uses NAT).
To perform an upload of both devices an Agent is required inside the OT Network. It is still required to allow communication from the versiondog Server to the Agent but the Agent only uses two ports and allows “direct” communication to both devices.
(Note: It would also be possible to make one PLC directly available using port forwarding on the “Industrial router”. This requires detailed know-how about the devices and is not always possible.)
Distributed network
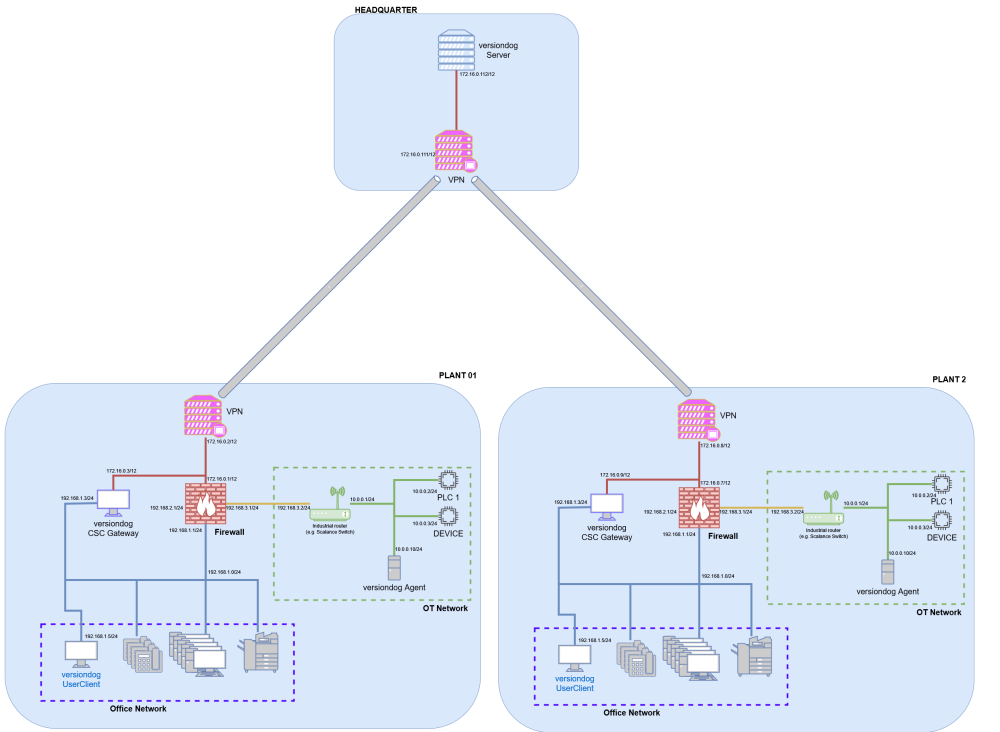
The network is segmented into different zones as before. The difference is that multiple versiondog UserClients can now connect to the versiondog Server using a special versiondog Client-Server-Communication (CSC) Gateway. This Gateway can bypass the Firewall and ensures that only versiondog communication is allowed.
This is useful in cases where the network is constructed using multiple Firewalls and the (re)configuration of each Firewall would end being a complicated task. One versiondog Server could be used to connect to multiple locations. As a security measure we recommend the use of VPN for all communication which is transmitted over untrusted networks (for example, internet).
Agent connection via Gateway
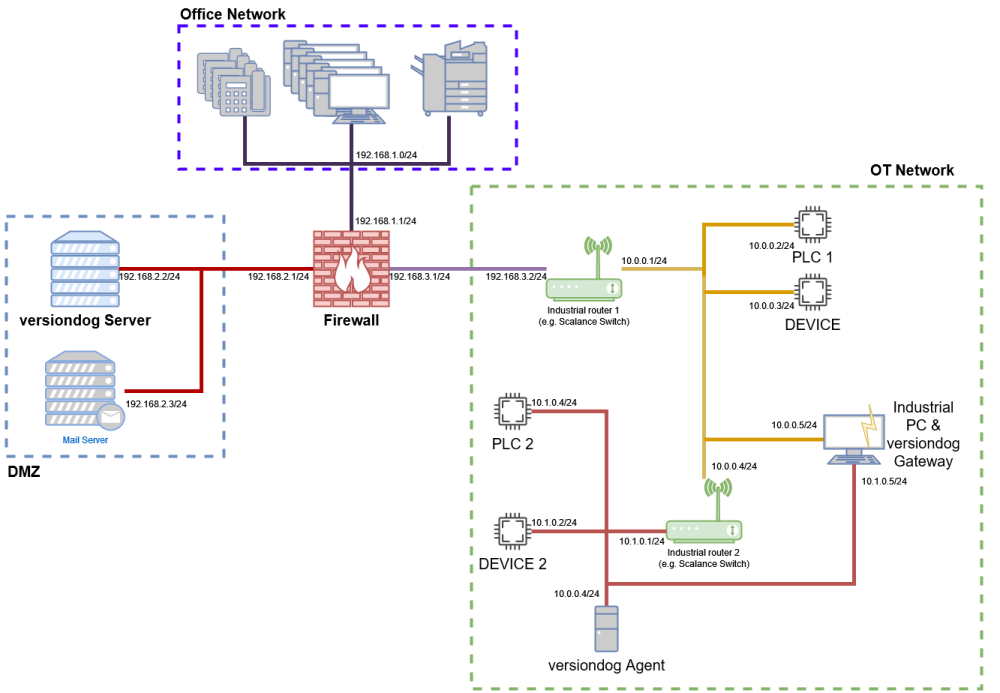
Image: Diagram Agent Connection via Gateway
In this network scenario a dedicated subnet/subnetwork (10.1.0.0/24) was introduced in the OT-Network. Only two devices must be available for backups.
As we have two "Industrial routers" which provide NAT we can place a versiondog Agent inside the last NAT network (for example, the subnet with the most hops when viewed from the versiondog Server). To be able to connect to the Agent, we have multiple options:
-
Using a versiondog gateway
The first router ("Industrial Router 1") must be configured to forward incoming connections to the versiondog gateway. The Gateway itself will automatically forward all requests to the versiondog Agent. No configuration changes needed on the second router! -
Configure the router to forward connections
As before the first router "Industrial router 1" must be configured to forward incoming connections. this time the connection is forwarded to the second router. The second router ("Industrial router 2") must be configured to forward the incoming connection to the versiondog Agent.
In both cases the Agent can reach all devices in the subnet 10.1.0.0/24 and all devices in 10.0.0.0/24. (Remember: The second router already does NAT routing and forwards all requests to the 10.0.0.0/24 network.)
Two sites and multiple subnetworks
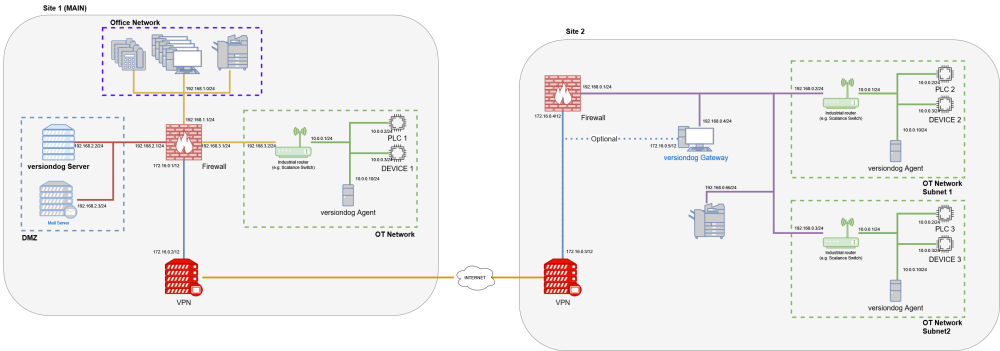
If multiple sites should be connected using only one versiondog Server this could be accomplished by using a VPN connection as before.
The routers of the OR-Network must be configured to forward the versiondog Agent connection. If multiple OT-Networks exist it could be useful to install a versiondog Gateway. This way only the Gateway must be reachable from the versiondog Server (remote site) and the connection is automatically routed between the OT-Networks. The Gateway could also be configured to directly connect to the VPN network and remove load from the Firewall devices.